|
|
|
See P5 Software for Gnutella in Action
"It was only a matter of time before they got caught."
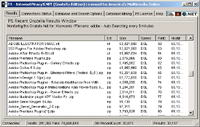 To the left you'll see the P5 Recent Results window using the Search criteria of "adobe". P5 lists the last 333 search results found here, and these can be searches P5 initiated, or others on the Gnutella Network did.
To the left you'll see the P5 Recent Results window using the Search criteria of "adobe". P5 lists the last 333 search results found here, and these can be searches P5 initiated, or others on the Gnutella Network did.
P5 uses your search criteria, finds results, and records enough evidence on the action of sharing the media to make it possible to prosecute the user/s commiting the crime/s.
P5 will Port, Track, Trace, allow you to Report and thereby Stop the illegal use of Gnutella.
P5 for Gnutella can also record to it's database the Gnutella Software used to commit the crime.
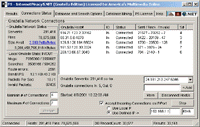 In the screenshot of P5 Software for Gnutella on the right, you can see the actual P5 Connections Status. Here is where P5 connects to the Gnutella Network and starts to record the evidence. Using our unique proprietary algorithms, P5 has the ability of searching the majority of the Gnutella Network, locating and contacting thousands of the hosts which yeilds the highest search results to hosts ratio. Beyond the search reach, P5 doesn't forward any search results - ever, essentially placing a roadblock in the Gnutella Network protecting and preventing further spreading of the media. In the screenshot of P5 Software for Gnutella on the right, you can see the actual P5 Connections Status. Here is where P5 connects to the Gnutella Network and starts to record the evidence. Using our unique proprietary algorithms, P5 has the ability of searching the majority of the Gnutella Network, locating and contacting thousands of the hosts which yeilds the highest search results to hosts ratio. Beyond the search reach, P5 doesn't forward any search results - ever, essentially placing a roadblock in the Gnutella Network protecting and preventing further spreading of the media.
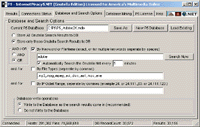 In this next screenshot to the left, we see the P5 Database and Search Options Window. This is where P5 Search Criteria is set. Because P5 is designed to run 24 hours a day, and possibly several weeks at a time, the data it gathers is recorded to it's database. You can have several P5 Databases and can load any of them at anytime, save them with a different filename for later reporting, or create a new one from scratch. The search options enable you to target your search, using AND meaning all criteria must match, or using OR meaning any search criteria can match. You may search for All files being shared, or by specific keywords or filenames, and even IP Octet/s. The IP Octet/s search is particularly important for ISP's wishing to enforce their Terms of Service, Countries or Law Enforcement Agencies wishing to target specific geographical internet locations, or any P5 Software Customer
needing to target specific ISP's or Geographical internet locations. IP Octet/s are what make up Internet Protocol Addresses, and you can search using any combination of A.B.C.D, or for multiple IP Octet/s seperated by commas like so (24., 63.12., 216.131.). In this next screenshot to the left, we see the P5 Database and Search Options Window. This is where P5 Search Criteria is set. Because P5 is designed to run 24 hours a day, and possibly several weeks at a time, the data it gathers is recorded to it's database. You can have several P5 Databases and can load any of them at anytime, save them with a different filename for later reporting, or create a new one from scratch. The search options enable you to target your search, using AND meaning all criteria must match, or using OR meaning any search criteria can match. You may search for All files being shared, or by specific keywords or filenames, and even IP Octet/s. The IP Octet/s search is particularly important for ISP's wishing to enforce their Terms of Service, Countries or Law Enforcement Agencies wishing to target specific geographical internet locations, or any P5 Software Customer
needing to target specific ISP's or Geographical internet locations. IP Octet/s are what make up Internet Protocol Addresses, and you can search using any combination of A.B.C.D, or for multiple IP Octet/s seperated by commas like so (24., 63.12., 216.131.).
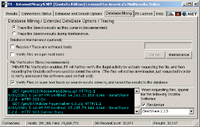 In this next P5 Software screenshot on the right, we can see the P5 Database Mining Window. Here you may run database maintainance by tracing any host not yet traced, or by determining the Gnutella Software used by the user. You may also trace the Gnutella Users geographical internet location as the search results come in, and also determine the Gnutella Software used as the search results come into P5. When you use the P5 File Verification, P5 requests the file from each unique user, masks itself as one of "them", records their Gnutella Software used to commit the crime, and closes the connection to them - not actually downloading the file. In this next P5 Software screenshot on the right, we can see the P5 Database Mining Window. Here you may run database maintainance by tracing any host not yet traced, or by determining the Gnutella Software used by the user. You may also trace the Gnutella Users geographical internet location as the search results come in, and also determine the Gnutella Software used as the search results come into P5. When you use the P5 File Verification, P5 requests the file from each unique user, masks itself as one of "them", records their Gnutella Software used to commit the crime, and closes the connection to them - not actually downloading the file.
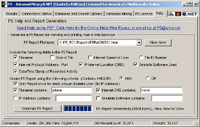 Finally, in the P5 Help Window, you may access the P5 Online Help, or access and Generate P5 Reports. A P5 report may be generated using any or all fields from it's current database, and you may search the database by filename, Internet DNS, IP Address Octet/s and Gnutella Software. Once you create the report, it is saved and stored where it may be viewed and printed from any web browser. Finally, in the P5 Help Window, you may access the P5 Online Help, or access and Generate P5 Reports. A P5 report may be generated using any or all fields from it's current database, and you may search the database by filename, Internet DNS, IP Address Octet/s and Gnutella Software. Once you create the report, it is saved and stored where it may be viewed and printed from any web browser.
Purchase P5 License/s Now
Each copy of P5 Software for Gnutella requires a P5 License. We sell P5 Licenses in single, 5 and 25 sets.
View sample P5 Reports
One Sample P5 report was created by P5 using it's database and the criteria of "Metallica" and targeting the ISP "home.com".
Have a Question? Contact Us.
Read the P5 Article from the Owner of America's Multimedia Online
|
 To the left you'll see the P5 Recent Results window using the Search criteria of "adobe". P5 lists the last 333 search results found here, and these can be searches P5 initiated, or others on the Gnutella Network did.
To the left you'll see the P5 Recent Results window using the Search criteria of "adobe". P5 lists the last 333 search results found here, and these can be searches P5 initiated, or others on the Gnutella Network did. In the screenshot of P5 Software for Gnutella on the right, you can see the actual P5 Connections Status. Here is where P5 connects to the Gnutella Network and starts to record the evidence. Using our unique proprietary algorithms, P5 has the ability of searching the majority of the Gnutella Network, locating and contacting thousands of the hosts which yeilds the highest search results to hosts ratio. Beyond the search reach, P5 doesn't forward any search results - ever, essentially placing a roadblock in the Gnutella Network protecting and preventing further spreading of the media.
In the screenshot of P5 Software for Gnutella on the right, you can see the actual P5 Connections Status. Here is where P5 connects to the Gnutella Network and starts to record the evidence. Using our unique proprietary algorithms, P5 has the ability of searching the majority of the Gnutella Network, locating and contacting thousands of the hosts which yeilds the highest search results to hosts ratio. Beyond the search reach, P5 doesn't forward any search results - ever, essentially placing a roadblock in the Gnutella Network protecting and preventing further spreading of the media. In this next screenshot to the left, we see the P5 Database and Search Options Window. This is where P5 Search Criteria is set. Because P5 is designed to run 24 hours a day, and possibly several weeks at a time, the data it gathers is recorded to it's database. You can have several P5 Databases and can load any of them at anytime, save them with a different filename for later reporting, or create a new one from scratch. The search options enable you to target your search, using AND meaning all criteria must match, or using OR meaning any search criteria can match. You may search for All files being shared, or by specific keywords or filenames, and even IP Octet/s. The IP Octet/s search is particularly important for ISP's wishing to enforce their Terms of Service, Countries or Law Enforcement Agencies wishing to target specific geographical internet locations, or any P5 Software Customer
needing to target specific ISP's or Geographical internet locations. IP Octet/s are what make up Internet Protocol Addresses, and you can search using any combination of A.B.C.D, or for multiple IP Octet/s seperated by commas like so (24., 63.12., 216.131.).
In this next screenshot to the left, we see the P5 Database and Search Options Window. This is where P5 Search Criteria is set. Because P5 is designed to run 24 hours a day, and possibly several weeks at a time, the data it gathers is recorded to it's database. You can have several P5 Databases and can load any of them at anytime, save them with a different filename for later reporting, or create a new one from scratch. The search options enable you to target your search, using AND meaning all criteria must match, or using OR meaning any search criteria can match. You may search for All files being shared, or by specific keywords or filenames, and even IP Octet/s. The IP Octet/s search is particularly important for ISP's wishing to enforce their Terms of Service, Countries or Law Enforcement Agencies wishing to target specific geographical internet locations, or any P5 Software Customer
needing to target specific ISP's or Geographical internet locations. IP Octet/s are what make up Internet Protocol Addresses, and you can search using any combination of A.B.C.D, or for multiple IP Octet/s seperated by commas like so (24., 63.12., 216.131.). In this next P5 Software screenshot on the right, we can see the P5 Database Mining Window. Here you may run database maintainance by tracing any host not yet traced, or by determining the Gnutella Software used by the user. You may also trace the Gnutella Users geographical internet location as the search results come in, and also determine the Gnutella Software used as the search results come into P5. When you use the P5 File Verification, P5 requests the file from each unique user, masks itself as one of "them", records their Gnutella Software used to commit the crime, and closes the connection to them - not actually downloading the file.
In this next P5 Software screenshot on the right, we can see the P5 Database Mining Window. Here you may run database maintainance by tracing any host not yet traced, or by determining the Gnutella Software used by the user. You may also trace the Gnutella Users geographical internet location as the search results come in, and also determine the Gnutella Software used as the search results come into P5. When you use the P5 File Verification, P5 requests the file from each unique user, masks itself as one of "them", records their Gnutella Software used to commit the crime, and closes the connection to them - not actually downloading the file. Finally, in the P5 Help Window, you may access the P5 Online Help, or access and Generate P5 Reports. A P5 report may be generated using any or all fields from it's current database, and you may search the database by filename, Internet DNS, IP Address Octet/s and Gnutella Software. Once you create the report, it is saved and stored where it may be viewed and printed from any web browser.
Finally, in the P5 Help Window, you may access the P5 Online Help, or access and Generate P5 Reports. A P5 report may be generated using any or all fields from it's current database, and you may search the database by filename, Internet DNS, IP Address Octet/s and Gnutella Software. Once you create the report, it is saved and stored where it may be viewed and printed from any web browser.